RETHINK DATA SECURITY
Get an overview of comforte Data Security Platform
comforte Data Security Platform
AUTOMATION
Use an AI-assisted network-based approach combined with repository scans to discover all sensitive data assets.
This includes “unknown unknowns”, meaning data in systems that you don’t know exist in your environment.
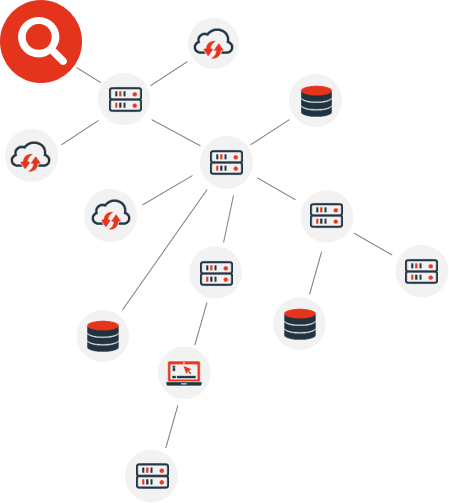
Automatically aggregate and catalogue all discovered data assets to create a PII inventory.
This continuous process also captures data mappings and data lineage of all copies of sensitive data.
Based on the insights from analyzing and classifying the data, define the optimal security strategy & policy for each data element.
Protect sensitive data-on-premises or in the cloud - while preserving data utility for processing and analytics.
Data elements get protected right from the moment of capture and stay protected throughout their lifecycle - at rest, in motion or in use.
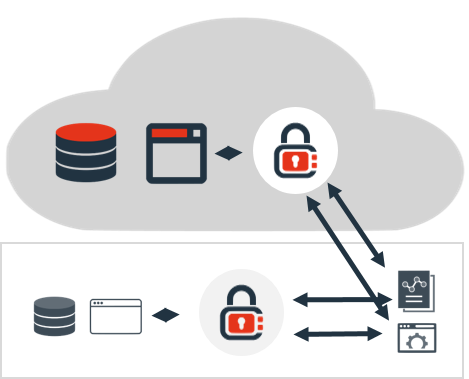
By providing multiple, flexible integration options with data flows & applications, we deploy ~10x faster than traditional solutions.
The platform follows a Data Security-As-Code approach to enable modern IT delivery and is a first-class citizen of container-based architecture.
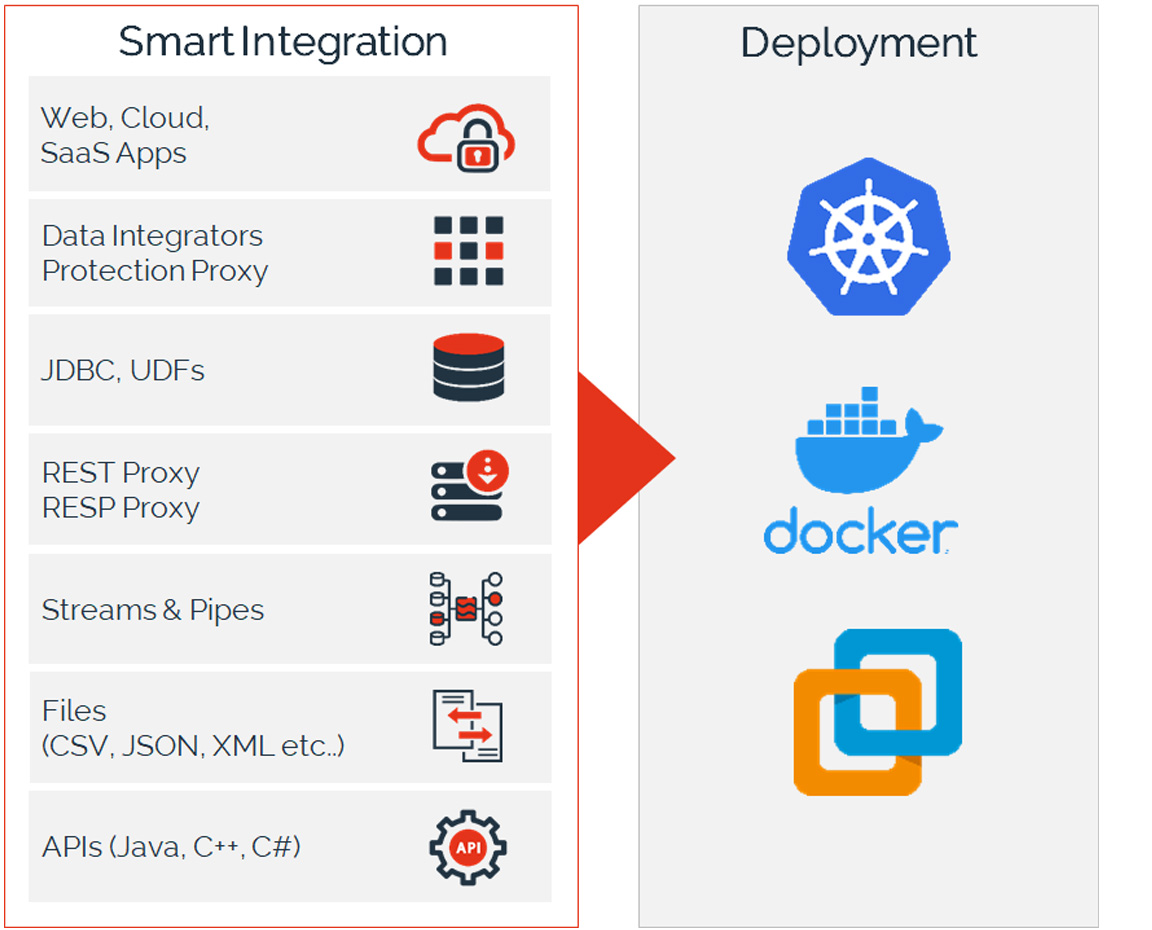
Why customers choose our platform
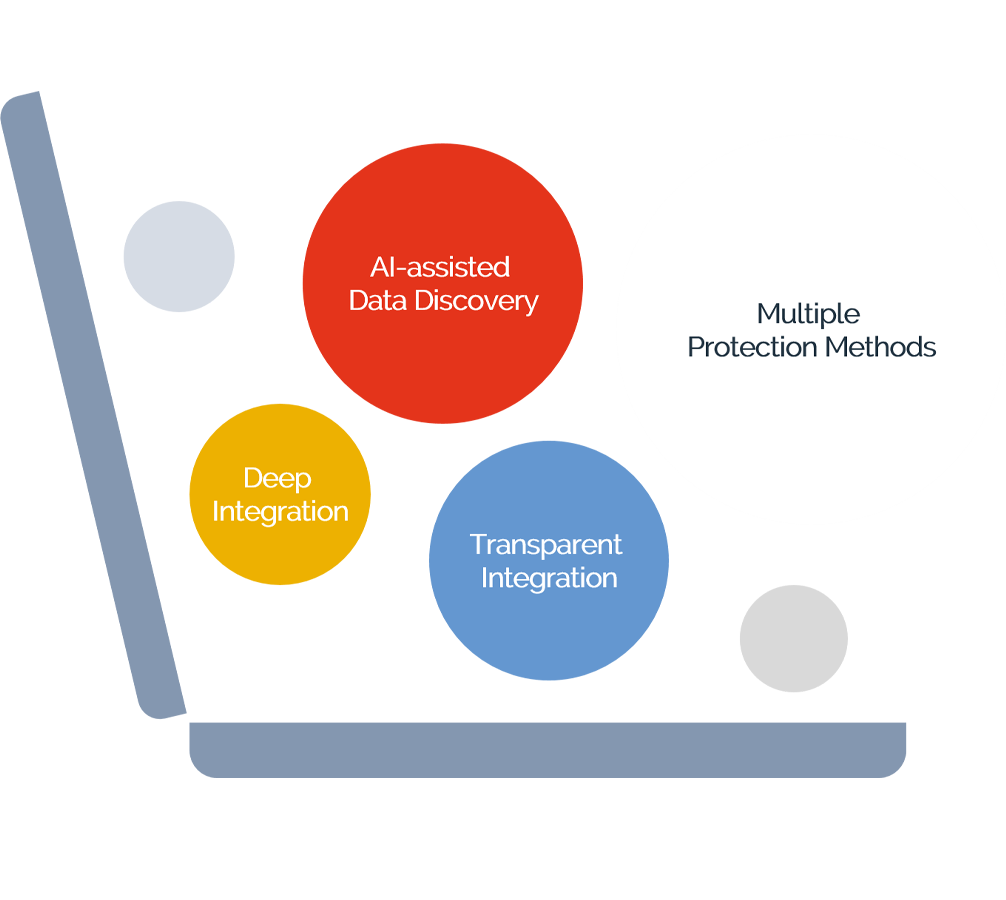
- AI-assisted Data Discovery that finds ALL sensitive data, including data in systems that you didn’t know existed
- Multiple protection methods for pseudonymization & anonymization while preserving data utility for processing and analytics
- Deep integration into Kubernetes and VMware combined with Data-Security-As-Code for DevOps & automation
- Transparent integration with data flows and applications for fast time-to-value
What industry experts say about us
Major US insurer takes its security to the next level
- Automated, continuous data discovery
- End-to-end protection for data privacy regulations
- More effective fraud detection and business insights
- Efficient data governance and risk reduction


DORA Compliance
Learn how the comforte Data Security Platform supports DORA compliance and addresses various DORA pillars with data-centric security.
Read the Fact Sheet