LEADING HPE NONSTOP SECURITY SOLUTIONS
Defend against increasing threats and protect your brand by securing sensitive data and locking down Nonstop systems
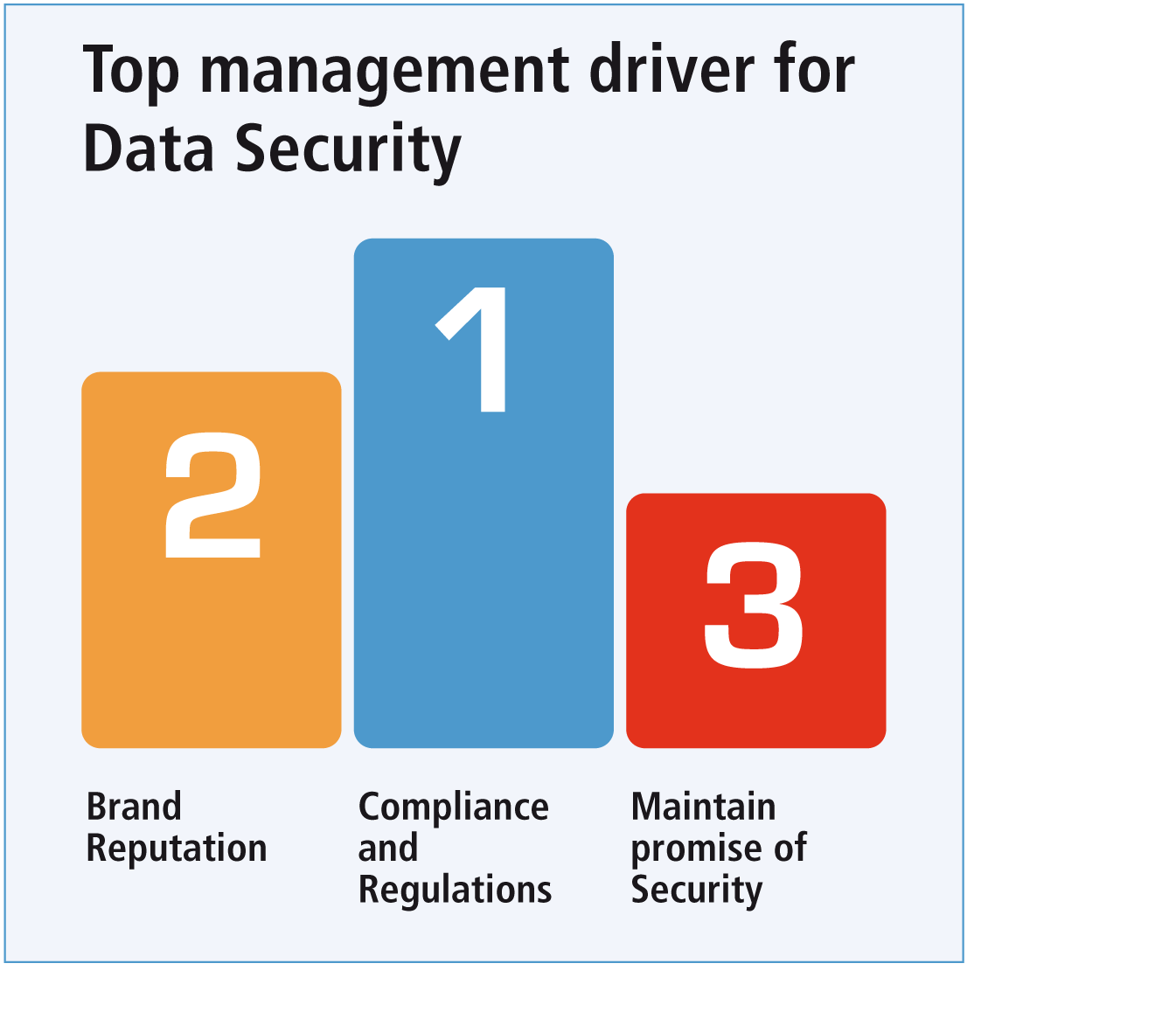
Data Security threats keeping you up at night?
NonStop systems drive your business and need sensitive data protected and systems locked down.
Organizations are constantly under attack and it is only a matter of time that a NonStop system will suffer a data breach or security incident.
Security professionals need to safeguard against numerous threats and possible security incidents.
NonStop systems require strong, effective security management and sensitive data protection to minimize risks of data exposure, and to keep the company brand in tact.

Data Protection and Security Framework
Lower Operational Risk and Reduce Compliance Burden by enhancing data protection and overall security
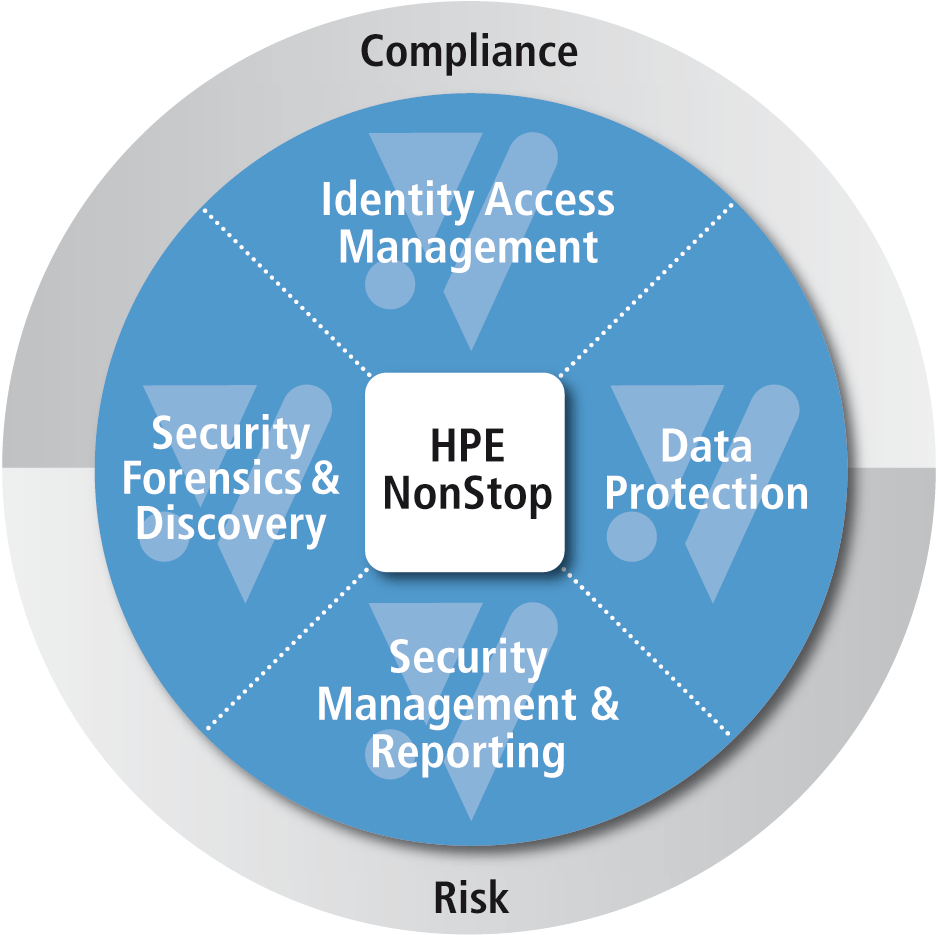
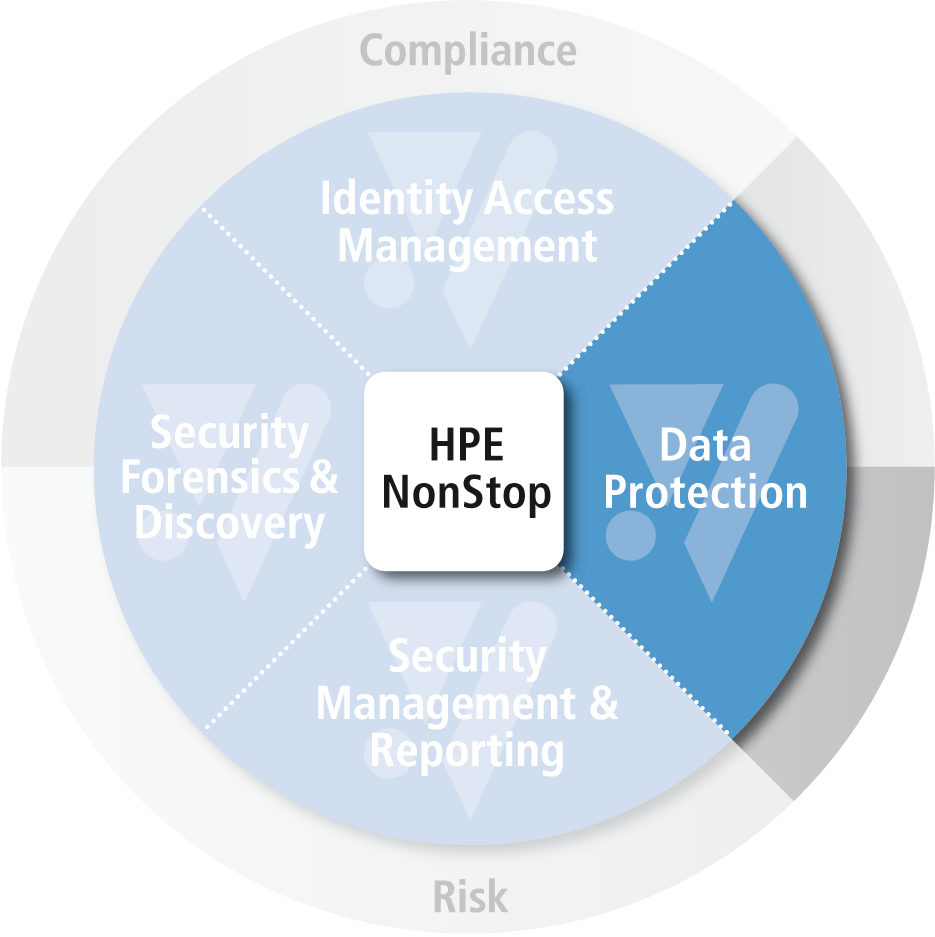
NonStop Data Protection
Perimeter and Layer defenses don’t always work to defend against malicious attacks as news headlines continue to demonstrate that attackers still get through.
Organizations need to protect sensitive data when it resides in files, database tables, or anywhere on NonStop systems. Data centric protection ensures that the data itself is protected and not left in a vulnerable state. Effective data centric protection reduces your risk of data exposure and minimizes the need for compensating controls when reviewing data protection regulations.
Data centric protection ensures sensitive data is not accessible by unauthorized people - inside or outside your network. Strengthen the overall data security hygene of your business by maintaining control over the sensitive data in which your company is responsible.
Protect Sensitive Data with Tokenization
Data-centric solution designed to protect sensitive data of any type with tokenization, ensuring no exploitable value
Expertly tuned to cause no noticable impact of the overall performance on mission critical NonStop systems.
Transparent integration works with any application on NonStop - so your dev teams are not required to modify your source code to activate data protection.
Recognized and approved tokenization method satisfies Data Protection requirements and regulations, which helps reduce compliance scope.
Download Factsheet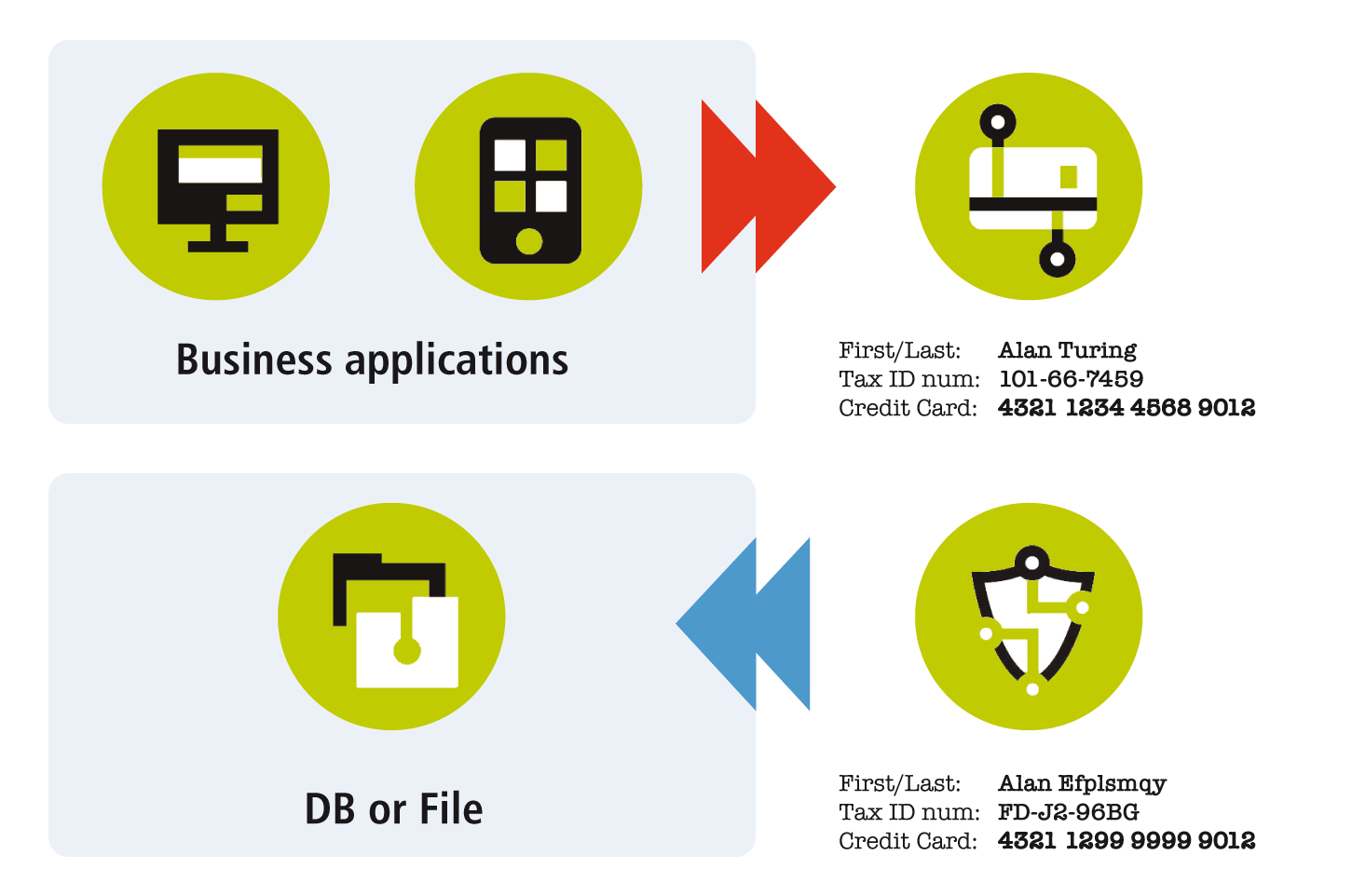
Secure Data in Motion
Turn on encryption anywhere in your network - between applications and databases, between your NonStop and other systems, and also from your NonStops to the outside world.
Flexible activation options including Transparent Integration, APIs, or simple library-calls, provide minimal setup time for your applications.
Encryption is supported by Data Protection requirements and regulations, and provides options for using existing key management and hardware security modules already in your enterprise.
Download Factsheet
Protect Sensitive Data on Backup Tapes
Contingency Plans must also ensure data collected is protected
Software-based solution requires no additional investment in backup hardware.
Seamlessly works with existing backup process
Download Factsheet
Security Management and Reporting
Let’s talk Security Management. Having multiple tools and solutions to administer security controls, access reports, and configure users, increases time required to implement Security controls and requires specialized skills and resources to get the job done. Not ideal for security teams with a large array of controls to implement.
A centralized Security Management platform reduces the effort and time it takes to configure, setup, or change security settings, in turn lets your team concentrate on more important tasks at hand. Incident alerts, access notifications, and audit reports can help reduce the time it takes to isolate a possible threat, determine severity, and answer critical security questions.
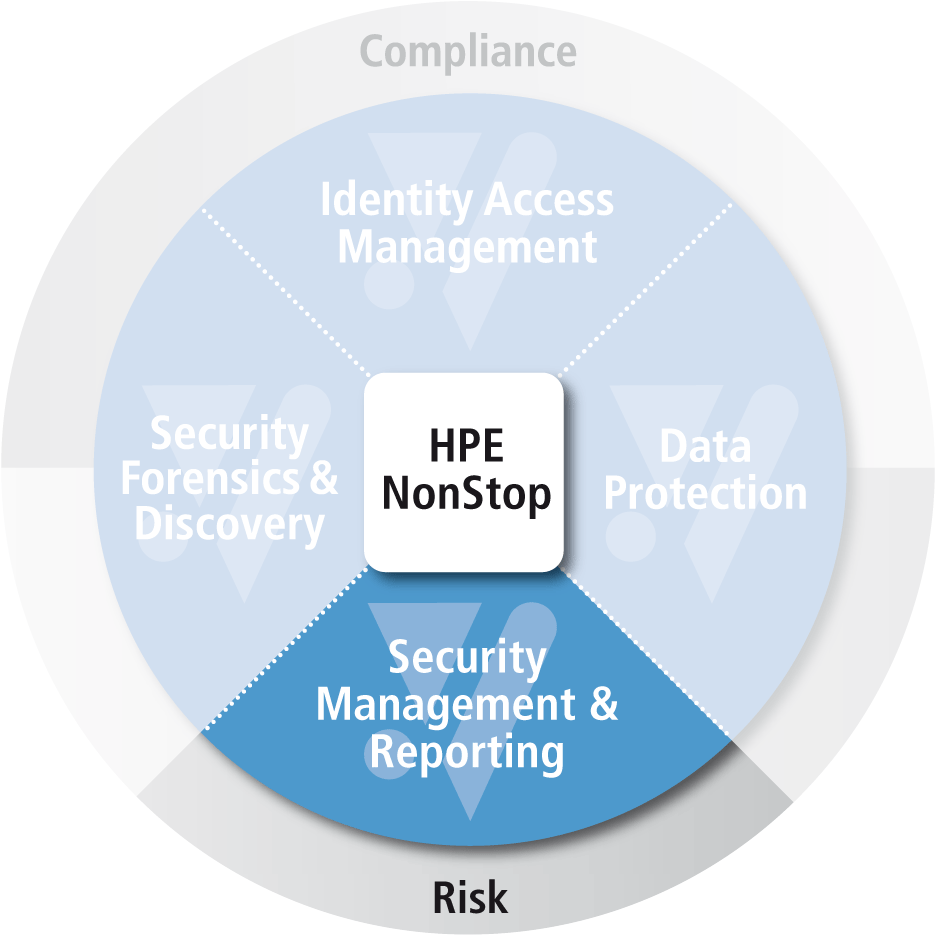
One-stop Security Management
comforte offers an intuitive, centralized interface that enables administrators to more efficiently and effectively manage NonStop security. Security administrators get a single solution for managing, monitoring and reporting upon multiple NonStop systems – which yields significant time and cost savings.
To ensure prompt action to minimize security incidents, security teams need real-time alarms and notifications. With comforte, notifications are easily sent to security teams or incident response personnel, and can also be sent to a Security Information and Event Management program (SIEM) should your company have a central SIEM is in place.
Download Factsheet
Identity Access Management
Free up security teams from the tangled web of identity access management. Centralize NonStop Safeguard™ user id creation and changes from command level controls into an easy to use Graphical UI. Span multiple NonStop systems to apply the same user ID changes quickly and easily.
People who need access to valuable data on NonStop systems, or who need to gain access to perform simple tasks, can now have 1 less user ID and password to remember and maintain. Single-sign on eliminates the headache, and reduces risk of privileged user ID misuse.
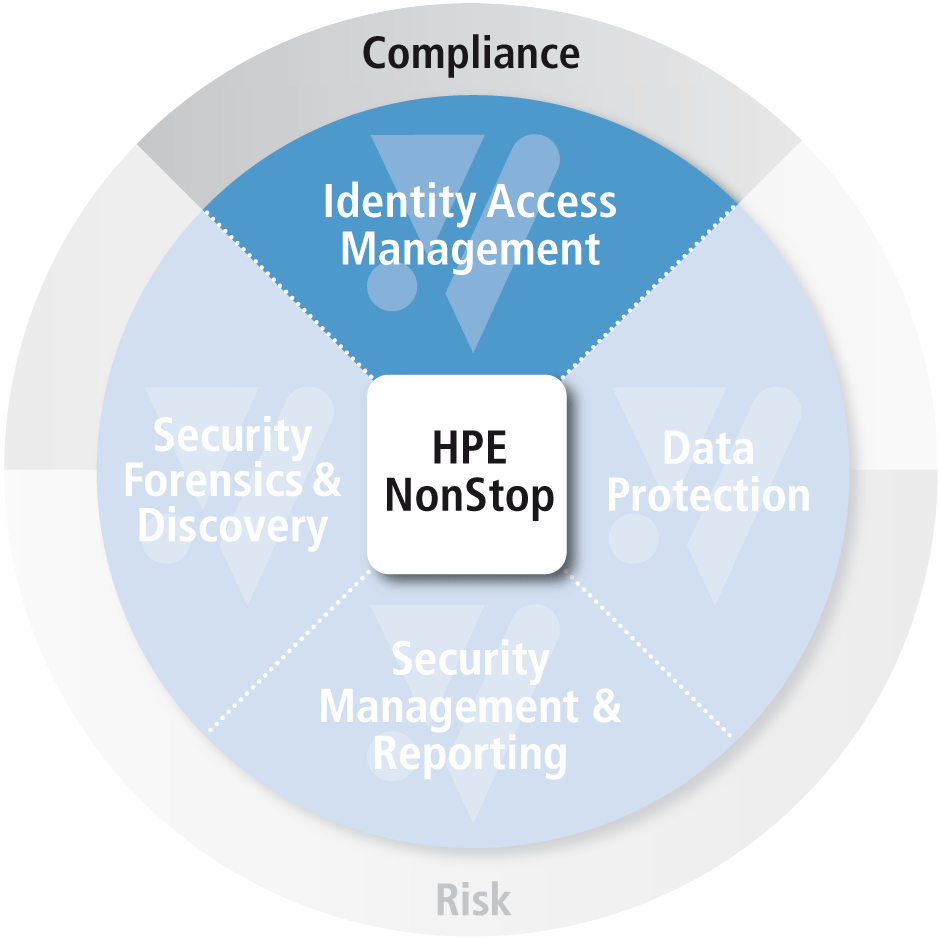
Manage User Access to NonStop systems
Integrate with Active Directory and with your Security central policies to configure single-sign-on user ids for NonStop systems
Download Factsheet
Forensics and Discovery
Provide Security teams with the tools they need to investigate security incidents quickly, without having to comb through mounds of EMS logs.
Forensics returns confidence to management by tracking and monitoring all access to applications and system resources, and identifies changes to critical files. Specifically for companies who handle payment card data, discover subvolumes and files containing unprotected payment cards, which ultimately helps achieve PCI DSS compliance.
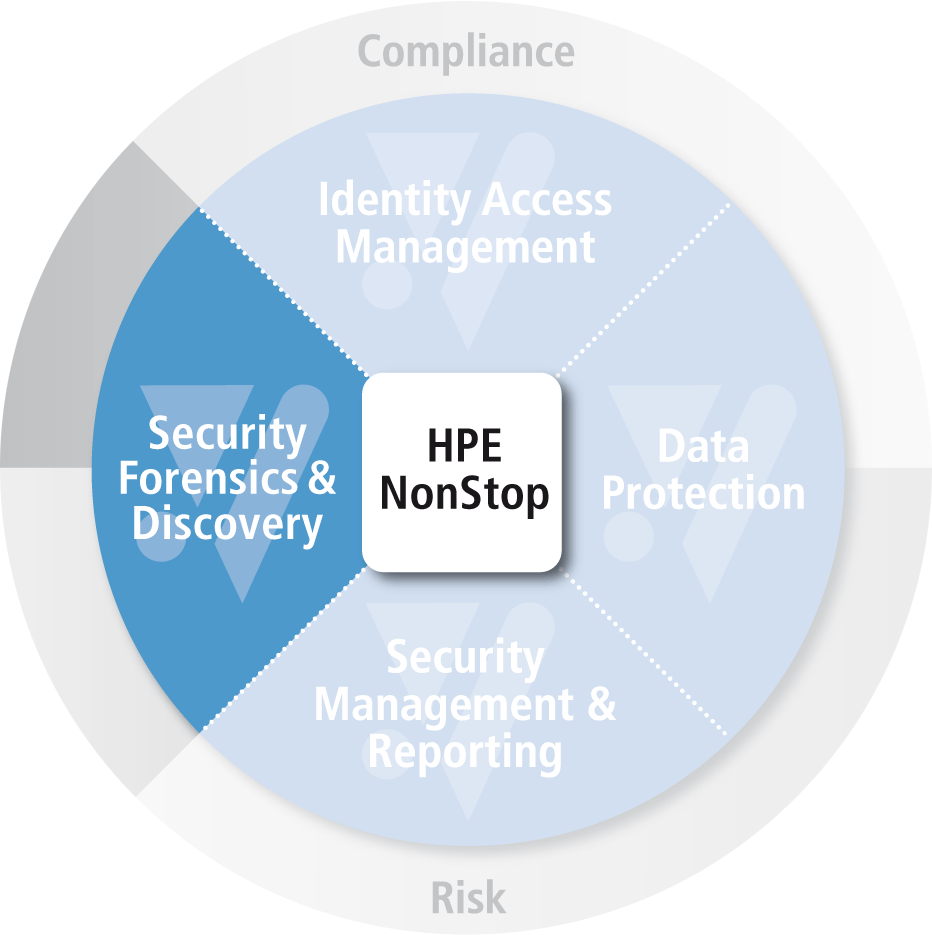
Anomaly Detection
Once hackers compromise a system, they may snoop around for days or weeks before exfiltrating data. Deploy detection methods to quickly determine if erroneous keystrokes are happening, if a virus or malware may have been installed against a file, or simply to determine if there are exploitable credit card numbers on your NonStop system.
Download Factsheet
Credit card numbers are hard to find
Think you know where every single credit card number is located, in every subvolume on your Production, Development, Test, and QA NonStop systems? Finding credit card numbers is challenging. Easily discover if and where there are exploitable credit card numbers on your NonStop systems.
Download Factsheet